Executive Summary
During a Proof of Concept (POC) deployment of CrowdStrike Falcon Endpoint Security, a customer unexpectedly uncovered active malicious behaviour within their environment. What initially appeared to be new detections triggered by the POC was later confirmed to be evidence of a previously successful attack that had gone undetected by the customer’s endpoint protection solution. Further investigation revealed that an unauthorized user account had been created earlier using administrative privileges, strongly indicating attacker persistence. Although the compromise predated the deployment of CrowdStrike, the installation of the Falcon agent immediately surfaced the attacker’s ongoing activity, enabling rapid containment and preventing further impact.
Background: A POC That Exposed the Past
The customer initiated a CrowdStrike POC to evaluate its endpoint detection and response capabilities. As part of the assessment:
CrowdStrike Falcon agents were deployed on selected systems Shortly after deployment, multiple high-severity detections were observed The customer engaged our team for immediate validation and guidance During discussions, the customer disclosed a prior security concern: a new user account had been created using administrative access, but the root cause had not been identified at that time. This information became critical in correlating the new detections with historical compromise activity.
Investigation Findings
Confirmed Indicators of Compromise (IOCs)
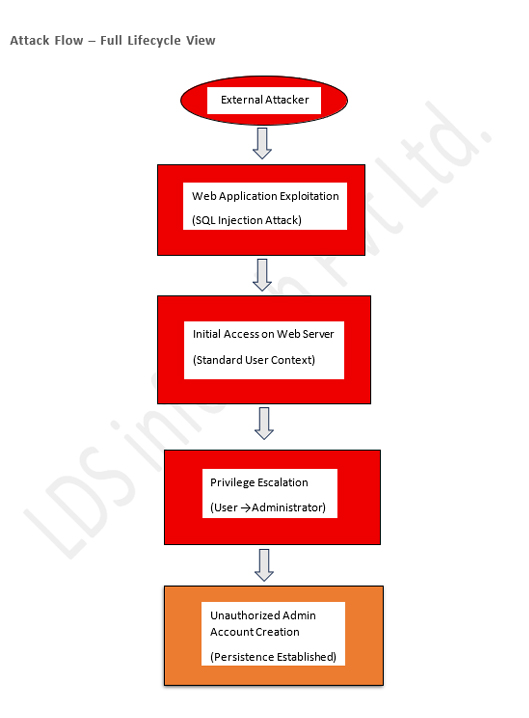
The investigation confirmed that the environment had already been compromised prior to the POC:
- Unauthorized administrative access had occurred
- An attacker-created user account existed with elevated privileges
- Malicious activity originated from a web application entry point
- SQL injection was identified as the likely initial attack vector
- Attempts were made to execute commands and abuse privileges via CLI
These findings validated that the attacker had successfully established a foothold and persistence well before CrowdStrike was deployed.
Why This Was a High-Risk Incident
The attacker had successfully obtained administrator-level privileges, enabling the creation and manipulation of user accounts—one of the strongest indicators of long-term persistence. With elevated access, the attacker was positioned to:
- Execute privileged system operations
- Maintain long-term access
- Move laterally across connected systems
Without detection, this level of control could have resulted in data exfiltration, ransomware deployment, or a widespread breach, significantly amplifying both security and business risk.
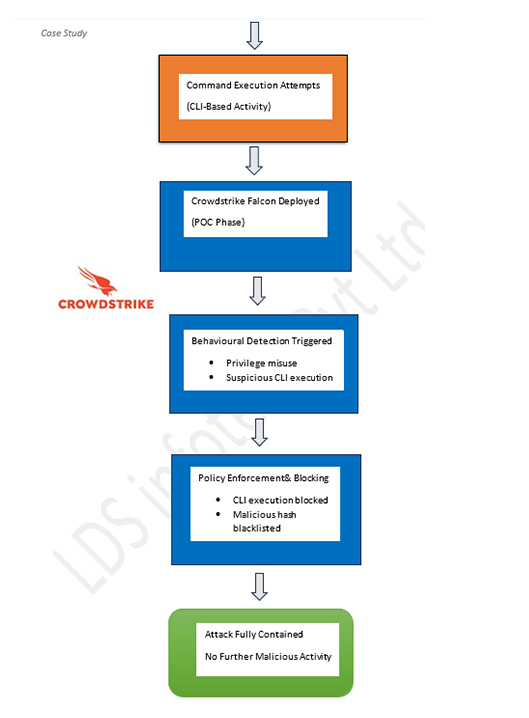
CrowdStrike’s Impact
Upon deployment, CrowdStrike Falcon immediately exposed the attacker’s behaviour, providing full visibility across the entire attack chain—from initial compromise to privilege escalation and command execution attempts.
Key outcomes included:
- High-confidence, behaviour-based detections
- Clear forensic evidence with no false positives
- Complete situational awareness for the customer
This time, the customer was able to accurately assess the scope of the compromise and confidently contain the threat.
Containment & Response Actions
Actions executed during the response session:
- Blocked CLI execution through Falcon policy enforcement
- Added the identified malicious hash to the blocklist
- Continuous monitoring for any further suspicious activity
- Recommended credential resets and a full privileged account review
Result:
No further malicious activity was observed after containment.
Impact Assessment
✔ No further exploitation detected
✔ No confirmed data loss
✔ No lateral movement identified
✔ No downtime or service disruption
Recommended Preventive Measures
1. Patch all operating systems and web applications
2. Conduct a comprehensive web application vulnerability assessment
3. Review and remove all unauthorized administrative accounts
4. Reset credentials for all privileged users
5. Maintain continuous EDR monitoring with CrowdStrike Falcon
Key Takeaways
- Attackers often establish persistence long before detection
- Unauthorized user creation is a strong indicator of compromise
- CrowdStrike detects behavior, not just known malware
- Even during a POC, EDR can uncover real and active threats
Conclusion
This incident clearly demonstrates that what you don’t see can hurt you.
CrowdStrike Falcon did more than validate a Proof of Concept—it uncovered an active compromise, revealed attacker persistence, and prevented further damage. What could have evolved into a serious breach was transformed into a controlled, well-managed security incident, providing the customer with both enhanced protection and renewed confidence in their security posture.
Author : Vanshita Shejwal, Network Security Engineer